Well let us define Steganography first. According to Wikipedia:
“Steganography is the art and science of writing hidden messages in such a way that no one apart from the sender and intended recipient even realizes there is a hidden message. By contrast, cryptography obscures the meaning of a message, but it does not conceal the fact that there is a message.”
So it is all about information hiding, today I will not get into the different techniques of steganography . I will just talk about one of my project that I used steganography in it.
It was required to implement an application that will be able to sign files digital using the RSA Algorithm.
The application provides some features and they are listed as follows:
1. Signing Files: Files can be signed and store the signature inside it or in another separate file
2. Signing Wave Files: The application signs wave files by signing the header of the file and then store and hide this information inside the wave file
The operation of the file signing is divided into three states:
1. Hashing:
In this operation we read the data that is going to be hashed. Depending on the hash function provided by the framework, you can hash the data in order to be ready for the next step.
 2. Signing:
2. Signing:In this operation we are going to sign the data received from the previous step. All we have to do is to encrypt the provided data using the private key of the user.

Here is the method I used to sign the data:
public byte[] SignData(string data, HashType hashType)
{
HashWrapper hasher = new HashWrapper(hashType);
byte[] bytesArraySignedValue = rsa.SignData(HelperFunctions.ConvertStringToByteArray(data), hasher.GetHasher());
SignedValue = HelperFunctions.ConvertByteArrayToHexString(bytesArraySignedValue);
return bytesArraySignedValue;
}
3. Verification:
In this step we are going to verify the signature. In order to do that we have to hash data and keep the digest, then decrypt the signature using the public key. Both should match in order to be a valid signature.
Here is the method I used to verify the signed data:
public bool VerifySignedData(string data, HashType hashType, byte[] signature)
{
HashWrapper hasher = new HashWrapper(hashType);
return rsa.VerifyData(HelperFunctions.ConvertStringToByteArray(data), hasher.GetHasher(), signature);
}
It seems that Microsoft has done all the work for you ;)
I will give you a breif about reading wave files in C#, For more information regarding reading wave files format please refer to the following link. The WAVE file format is a subset of Microsoft's RIFF specification for the storage of multimedia files. A RIFF file starts out with a file header followed by a sequence of data chunks. A WAVE file is often just a RIFF file with a single "WAVE" chunk which consists of two sub-chunks -- a "fmt " chunk specifying the data format and a "data" chunk containing the actual sample data.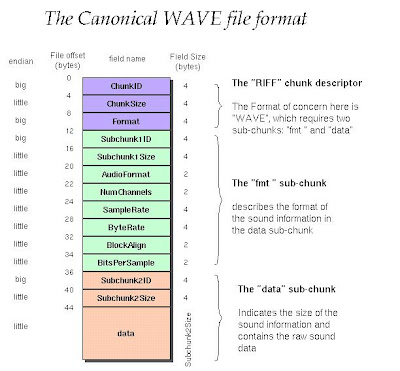
I used a new idea by signing wave files. Signing wav files operations is similar to signing a normal file. First, we have to calculate the signature of the input file but instead of calculating the digest for the whole file. We will calculate the digest for the header only. Then encrypt this hash using the private key. The only difference is the storing operation. We will store the signature bits, by changing the least significant bit in all the wave samples according to the signature bits. This bit won’t make a difference in the sound of the file and we will have the digitally signed.
Application Logical Design:
*Logging Module: This module is responsible for the logging functionality across all the application
*Helper Classes: This module includes some common functionalities like handling the bit manipulation using the c# language
*Wave File Module: This module is responsible for handling the wave operations: Reading wave binary data, writing a new wave file and signing the wave files
*RSA Wrapper: This module wraps the functionality of the RSA algorithm. It facilitates the using of encryption depending on the application logic
*Hash Wrapper: This module is responsible for wrapping the hash algorithm. It uses the hash service providers available through the dot net framework
*Presentation Layer: This module is responsible for handling the UI functionalities across all the application
I used Visual C# 2005 to implement this application. I am sharing the source code, I hope it could be helpful. You can find it here. Pleas let me know your feedback.

Download: DigitalSigner.zip


9 comments:
great article and very useful... would be nice to be able to save a decrypted wav file after validating the signature
great article... and most interesting is the idea of hidding the wave file signature using the least significant bit, nice :-)
this is not working for a file. i tried signing a .doc file and later verifying it after making changes but it again shows verified hence this code is not for files
Actually embedding the signature inside a doc file requires another technique other than changing the least significant bit. using the developed algorithm on a doc file will corrupt it.
I will try to think for another way to sign a doc. I think Microsoft has its own digital signing techniques for Word Documents.
Just a thought: I had a quick look at your application, what you're doing seems to me not to be steganography but digital watermarking (they are two different things, although they are like sisters).
Hello Fady,
Do you have any procedure document to execut your code. I am new to this area and bit struggling to execute your application.
Kindly help me on this.
Can you please send it to my id venkat.kaashiv@gmail.com
Cheers,
Venkat
very usefull article...
very usefull article...
very usefull article...
Post a Comment